Frequently Asked Questions










- OS
- Processor Model/Frequency
- Ram Quantity
- Local IP Address
- Wan IP Address
Are important action records kept?
Yes. Access information of all activities is kept in Perwatch. The client can receive reports at any time to be used as evidence when necessary.
Do you share our data with others?
No, we do not share. Perwatch never sells your personal data to anyone else and does not share it with third parties. We try to be as open as possible about this. Your personal data belongs to you.
Do you want an admin access for integration from our Active Directory server?
No. Perwatch connects to user session id. Therefore, it has native Active Directory compatibility. Whoever logs in to the computer via AD automatically continues to follow that person from where he left off. In case of a possible format or computer change, you just include the computer in the name and install the perwatch agent. That’s it.
Frequently Asked Questions
Perwatch is a comprehensive personnel monitoring, personnel monitoring and evaluation software. It measures and evaluates the performance of white-collar personnel by monitoring their computer activities and gives you the most realistic performance and cost values. It prevents possible illegal activities and protects your company.
Yes. With the overtime module, you can organize weekly shifts and determine
the hours to follow the personnel. Perwatch will not transmit information
outside of these hours.
Yes, you can define it. By entering the break times in the overtime
definition groups, you can determine when the staff will take a break.
Not for now, but in our next major update, staff will be able to work
according to the dynamic overtime system. By choosing the project they will
work on, they will be able to start and stop their shifts whenever they
want.
Yes. For Perwatch, you can create separate shift groups for the company,
department and personnel and arrange the hours to be followed by the
personnel according to your needs.
Yes you can. Thanks to the Perwatch cloud system, it is possible to follow the instant actions of your employees wherever they are in the world.
Of course. For many important operations, monitoring continues even when there is no internet, by keeping internal records. As soon as the tracking software is online, it synchronizes the recorded data with the cloud. Thus, many activities can tracked even when there is no internet access.
Currently, all Microsoft Windows operating systems Windows 8 and above supported. For macOS, we have support for versions starting from Catalina and later.
It’s pretty short. The system prepares a special installation application for you. You complete the installation on the computers to be followed without the need to answer any questions or enter information. If you have an active directory system, you can finish the installation on thousands of computers in a few hours.
Yes, we can. As soon as the system does not detect activity for a certain period of time, it senses that the personnel is outside and activates the outside mode in order not to make a wrong calculation. The manager can decide how long this period will be by looking at his own internal operations. The customer can adjust this time between 1 minute and 60 minutes.
No. Perwatch is a productivity analysis focused software. It does not collect data such as keyboard inputs, camera recording, audio recording.
You can turn on the masking feature of screenshots in Perwatch. This feature makes the characters in the screenshots blurry. Thus, unnecessary data collection is prevented. We’re also working on a feature in our development plan where staff can temporarily pause tracking by starting the “Personal Time” mode. We aim to put this feature into service as soon as possible. As another feature, you can determine the hours your staff should work by using the overtime plan feature. Thus, the system will only follow up between the specified hours.
Yes. We have a trial version. You can test all its features without restrictions for 7 days.
Although Perwatch does not currently offer a full-fledged inventory module, it does provide you with computer hardware and network information used.
- OS
- Processor Model/Frequency
- Ram Quantity
- Local IP Address
- Wan IP Address
You can access the information with Perwatch.
Not for now. However, desktop control for remote support is included in our development plan.
Yes. Perwatch offers native AD support. Since it follows the user accounts, the user follow-up continues from that account, from whichever computer the user logs in. Even if you format the computers, all you have to do is restore the Perwatch application after the operating system is joining in the AD environment. In this way, the tracking will continue without interruption and the user profile will be intact. We offer the ability to transfer computers within non-AD computers and switch computers between users.
Yes. There are MSI packages in Perwatch. You can install these packages unattended. If you want to uninstall it, you can uninstall the application by selecting the computers from the Perwatch panel.
Not yet. However, an ITSM module will be available for your needs in the near future.
Yes. Our application supports many virtualization technologies and works seamlessly.
Perwatch is optimized to use very few resources. It uses very little ram and CPU resources. It can run smoothly with 2 processor cores and a minimum of 4gb ram.
Yes. With Perwatch, you can remotely restart computers, shut down, or log off users.
Yes. With the computer locking feature, you can close the computer to user access. When a computer is locked on your side, keyboard and mouse inputs are canceled and nothing appears on the screen except a warning with a message you want.
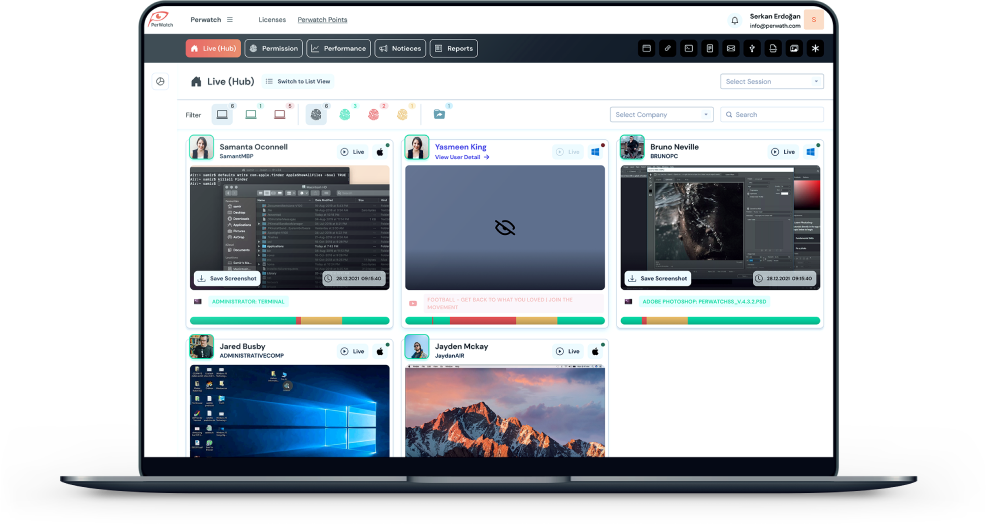
Of course. With Perwatch, you can get reports instantly, or by selecting specific time intervals. In Perwatch, it is possible to get reports of almost as many activities down to seconds. These reports can as detailed information for personnel productivity analysis as for investigating a legal issue.
No, with Perwatch, you get a wide range of information. How much did the staff participate in the work that month? How many points did they produce? Did they complete their working hours? It is possible to get many results, such as how much time you spent in which productive application, what is the performance situation within the company.
They can request separate reports for personnel and departments through the system. The report can produced instantly or it can be sent automatically by determining weekly and monthly periods.
Yes. There are special warning rules in Perwatch. You can create these rules according to your own needs and receive instant notification when an action related to this rule occurs. You can prevent problems before they grow.
Not necessary. Perwatch allows for a period to open reports sent to e-mails without login. After a certain login, it stops opening reports sent by e-mail for security purposes. If a report is needed again, it can download again by accessing its copy in the Perwatch interface.
There is no code in the Perwatch tracking endpoint software that can cause files to be sent from computers or the computer to be hijacked. Our servers are protected by globally accepted security techniques and systems. Data on the cloud is kept by AWS. Although the locations of the servers vary according to some continents and countries, GDPR compliance is of great importance to us.
No. The data processed by Perwatch is designed in such a way that it cannot be accessed by our employees without authorization from the customer. If a situation occurs in the customer account that requires access, the customer can temporarily grant Perwatch access from the settings menu. Even if the customer forgets to withdraw the permission after a certain period, it automatically removes the permissions.
Of course. With Perwatch, you can get reports instantly, or by selecting specific time intervals. In Perwatch, it is possible to get reports of almost as many activities down to seconds. These reports can as detailed information for personnel productivity analysis as for investigating a legal issue.
No. There is a temper protection on the application. File locations are hidden. If the application is closed, it will open again. If deleted, it can restore itself again.
Yes. Access information of all activities is kept in Perwatch. The client can receive reports at any time to be used as evidence when necessary.
No, we do not share. Perwatch never sells your personal data to anyone else and does not share it with third parties. We try to be as open as possible about this. Your personal data belongs to you.
No. Perwatch connects to user session id. Therefore, it has native Active Directory compatibility. Whoever logs in to the computer via AD automatically continues to follow that person from where he left off. In case of a possible format or computer change, you just include the computer in the name and install the perwatch agent. That’s it.
Internet activities, Program usages and Title information are processed.
Yes. Perwatch is also a LOG application. Information such as how many seconds the personnel stayed on which page or program is kept with detailed date information. This information can also be exported as PDF by reporting later. It makes your work easier for internal threat detection or a legal need.
Usage data remains in the system as long as the customer wishes. With the deletion of the company, we also deleted all the recorded data of the customer.
Certainly. We offer detailed productivity and usage analytics on a daily, weekly and monthly basis.
Yes. We are quite ambitious on this side. You can create department and employee specific productivity rules within Perwatch. For example, while facebook is a non-productive content for the accounting or production department, the marketing department can meet with customers from this platform and facebook can be a productive content for marketing. With dynamic productivity analysis, Perwatch offers you more accurate analysis.
Yes, we have. As soon as the system does not detect activity for a certain period of time, it senses that the personnel is outside and activates the outside mode in order not to make a wrong calculation. The manager can decide how long this period will be by looking at his own internal operations. The customer can adjust this time between 1 minute and 60 minutes.
Perwatch works incognito by default. We are working on a new version where the user can set their own working times and make their own choices within the application.