Adapt to Risks with Dynamic Alarm Rules
It is very important to detect risky actions on company computers in advance so that information not lost. With Perwatch dynamic action rules, you can instantly get a telegram alert when a rule you set is triggered and you can lock the computer or have it shut down. If you wish, the system can also collect evidence with the screenshots it constantly collects, allowing possible legal processes to be concluded faster and more smoothly.
- Rule-based Screenshot Collection
- Sending Alerts by Mail
- Getting Alerts With Telegram
- Generating Event Number
- URL, APP, USB Disk and File Activity Tracking
Action Related Screenshots
When an in-house research is required, it is important to know why the screenshots are taken. Otherwise, it will not be easy to find what you need among thousands of screenshots. Perwatch connects actions with screenshots. Thus, when you filter and find the process with parameters such as time, person, computer, you will automatically find the screenshots associated with it.
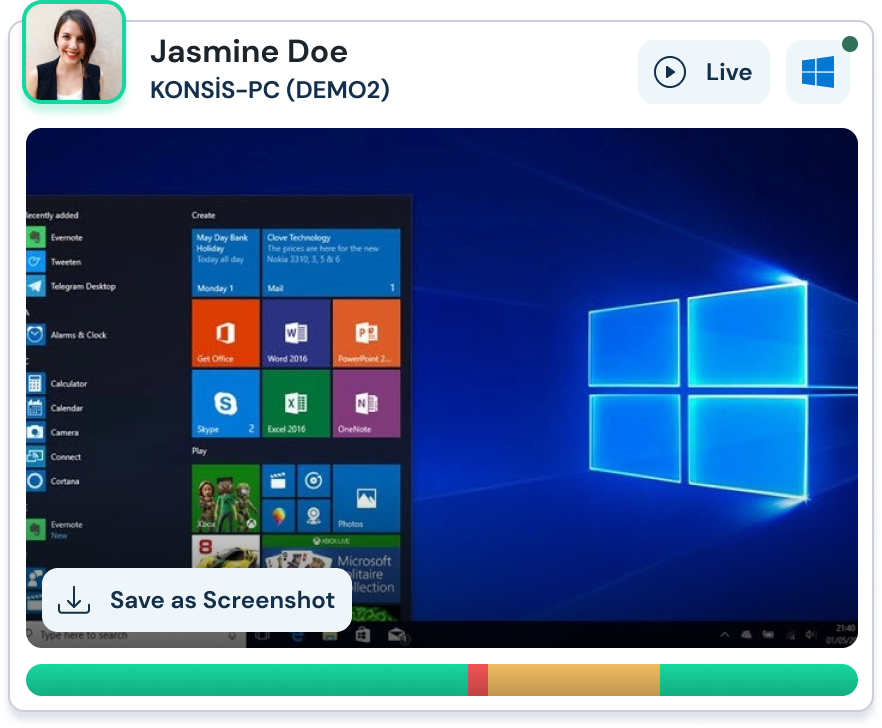

All File Actions Recorded
All computer operations are recorded second by second by Perwatch. Detailed log records are also kept in Perwatch along with time tracking. When this feature is enabled, every operation performed on the computer can be traced back even for every second. It will also be able to respond to SIEM needs by accessing information such as which folder was entered or how many seconds and when a web page was left.
USB Memory Control
Undoubtedly, file transfers made via USB memory sticks and devices constitute the first rank of data leaks in companies with a rate of 67%. With Perwatch, you control all USB memory movements in your company. You can ban USB sticks on all computers in the company or make them work only as read-only. With Perwatch, it is also possible to allow only designated USB sticks. The system will track every memory installed and removed from the system and report it to you instantly.


Image processing technologies have been used for a long time to prevent possible internal threats and gather evidence. Screenshots are automatically scanned with OCR and their contents are checked according to the company’s security parameters. With this technology, which is used for the purpose of masking personal data or protecting important data, a much faster search can be made within the actions and a safer environment can be created for the company by working together with DLP and SIEM technologies.
Light DLP
(Coming Soon)
Data containing intellectual property is now almost entirely computerized. It is essential to protect the important files that make up the competitive and sales power of companies, and it is getting more difficult to do this job day by day. Data protection systems are either very complex and require constant IT administrator intervention, or they are too complex to install. Perwatch is built on a simpler approach to complete blocking. We want it to hinder workability while protecting important files in a structure where administrators can give permissions more easily and the allowed transactions are recorded in detail.

With our powerful modules, we protect important information while tracking productivity.
Perwatch started off with the goal of solving the productivity needs of many sectors. We create a safe, productive and profitable system for your company with our desktop, mobile, iot and image processing technologies. You can contact us for your special needs.
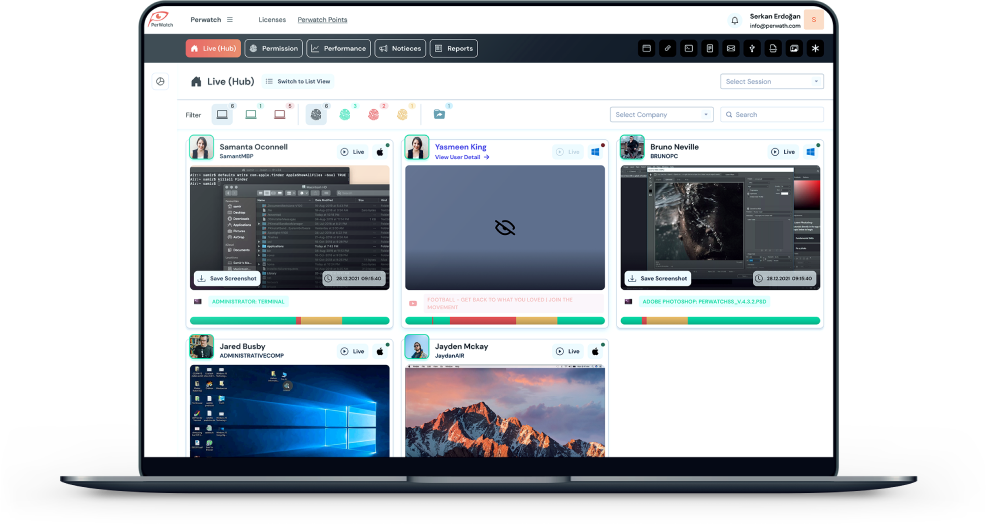
Employee Monitoring
See detailed activity reports of your employees and instantly access reports on their productivity.
E-Mail Tracking
Take control of your company's email traffic. Track customer relations and measure communication quality.
USB Memory Control
Monitor, block or allow USB sticks inserted into computers in your company.
Automatic ScreenShots
Access both the process and the screenshot with automatic screenshots linked to events.
File Activity Monitoring
Instant access to information such as file deletion, modification and moving on company computers and shares.
Video Recording
Watch events at any time interval with live video recording. Prevent possible risky actions before they grow.

Would you like us to call you? You can ask your questions to our teammates.
