Cost-Effective Threat Analysis
Protecting against potential internal threats is a costly process. Although a solution is reached with many applications and long efforts of IT departments, these processes can cause enormous costs and time losses for companies. Most of the time, the systems established by the companies can be so tight that they take away the employee’s ability to do business, and therefore companies can experience serious productivity losses. Perwatch provides low-cost SIEM feature to companies by monitoring data and detecting possible risky activities with its proactive approaches and creates the first line of defense required for data protection.
File Activity Tracking
It is a hard task to follow the movements of the files processed within the company. Sometimes knowing who did the transaction and when it can help solve potential problems before they grow. Perwatch also provides support to your company in data tracking and information security. With detailed reports and instant action alerts, it takes the lead role in protecting your files and early detection of possible risky actions.

USB Drive Control
USB memory leaks are at the beginning of the moments when data in companies lost the fastest. Checking who is inserting a USB stick or whether it permitted the inserted USB memory is very important for the protection of important data. Perwatch makes it much easier for information technology managers, thanks to its powerful modules for blocking and controlling USB memory sticks.
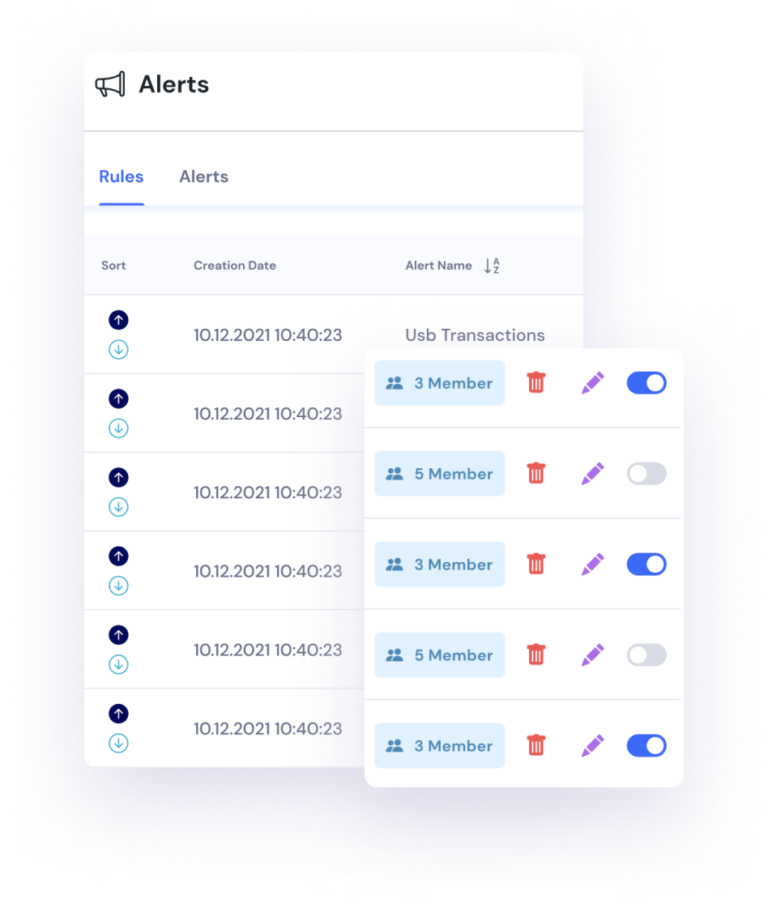
Alert Rules
It has become a necessity for companies to use security software to prevent internal and external computing threats. Ransom groups are constantly improving themselves and developing different attack methods. One of the most important requirements to prevent ransomware attacks is to use a strong intrusion prevention software and firewall, and to detect attackers who have managed to circumvent possible security applications in the system by supporting these structures with SIEM solutions. With Perwatch, you get cost-effective solutions for your SIEM needs. If it triggered an action you specify, you will receive an immediate warning and have the chance to prevent it before the security risk grows.
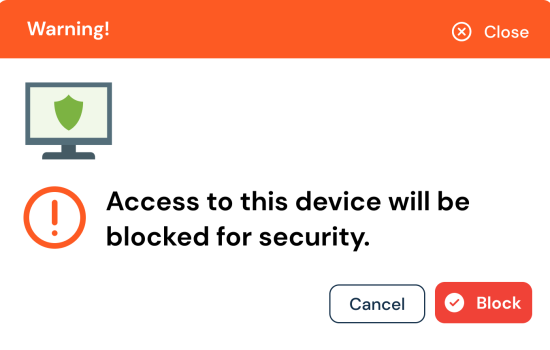
Computer Lockdown
If risky transactions detected, it may be necessary to take immediate preventive action on company computers. Sometimes locking a remote system or preventing potentially unwanted activities can prevent serious security issues and loss of information. When necessary, instant locking of computers can be achieved with Perwatch. With Perwatch, it is possible to detect and act instantly.
Email Tracking
Almost all successful companies are ahead of the competition because they can control information well and saw early the potential risks. It is very important to control the internal e-mail traffic in order to control the sales and order channels correctly and to measure the quality of the relations between the employees and the customers. With Perwatch, you can monitor all e-mail traffic and make the communication between staff and customers healthy.
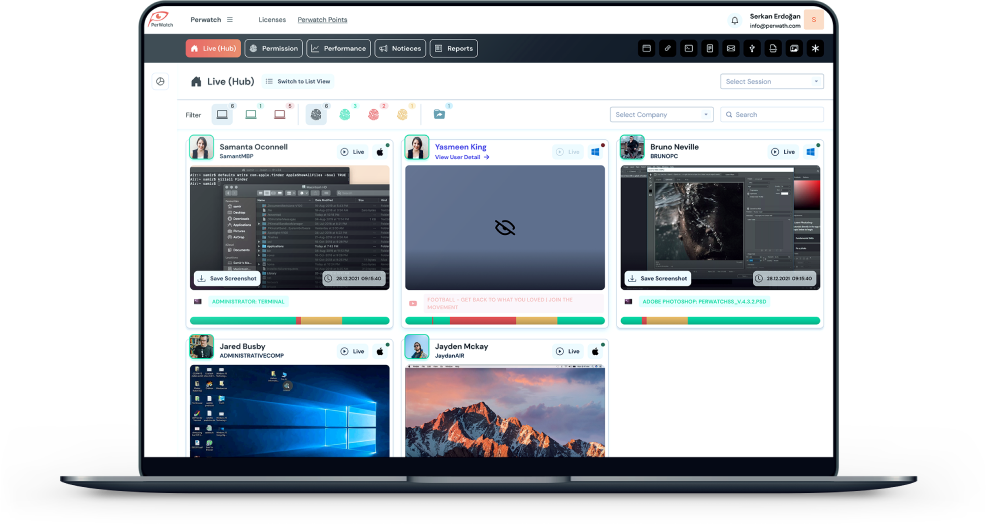
With our powerful modules, we help protect important information while tracking productivity.
Perwatch started off with the goal of solving the productivity needs of many sectors. We create a safe, productive and profitable system for your company with our desktop, mobile, iot and image processing technologies. You can contact us for your special needs.
E-Mail Tracking
Take control of your company's email traffic. Track customer relations and measure communication quality.
Automatic ScreenShots
Access both the process and the screenshot with automatic screenshots linked to events.
Alert Rules
Get notified immediately when an action you have set is triggered and create automatic proof with screenshots.
File Activity Monitoring
Instant access to information such as file deletion, modification and moving on company computers and shares.
RAW Usage Logs
Together with time tracking, we offer raw usage times and provide early diagnosis of a possible risky situation.
Evidence Collection
We collect evidence for events triggered by alarm rules and enable you to detect potential internal threats faster.

Would you like us to call you? You can ask your questions to our teammates.
